ProvenVisor: Empowering Embedded Devices with Unmatched Security
A secure hypervisor for virtualization solutions
What Is a Hypervisor?
ProvenVisor is a next-generation hypervisor specifically designed for embedded devices with high flexibility and high-security requirements. Leveraging the ARMv8-A architecture and hardware virtualization extensions, ProvenVisor enforces strong security properties on its Virtual Machines (VMs) while providing efficient access to essential resources.
With a minimal Trusted Computing Base (TCB) and explicit authorization for inter-guest communications, ProvenVisor ensures the highest level of security for your critical
applications.
Benefits | ProvenVisor.
With ProvenVisor, protect your embedded device with a high-assurance hypervisor designed for security:
Secure Multi-Tenancy:
Secure Multi-Tenancy: ProvenVisor allows you to securely run side-by-side guest OSs with varying levels of risk and trust on the same physical MPU. Whether mission-critical or non-mission critical, trusted or untrusted, each guest OS remains isolated and protected.

Enhanced Security Policies:
By utilizing ProvenCore, ProvenVisor can enforce sophisticated security policies on VMs requiring external communication. This includes filtering all incoming and outgoing communications, creating a robust defense system around guest OSs.

Facilitates Security Certification:
The formal documentation of ProvenVisor's security properties streamlines the security certification processes, saving time and resources.

Simplified Integration:
ProvenVisor seamlessly integrates with most common general-purpose OSs (e.g., Linux, Android), simplifying the integration process and ensuring optimal performance.
Designed for Security | ProvenVisor.
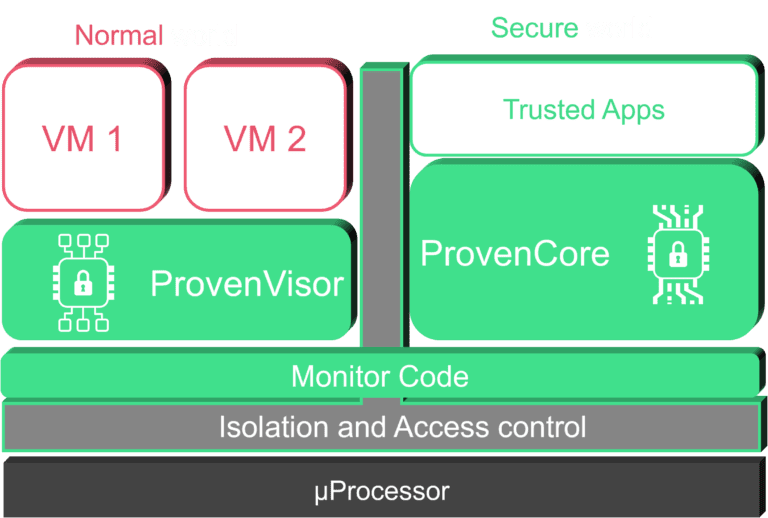
ProvenVisor has been designed from the ground up to ensure the security of the VMs it hosts, from its high-level architecture down to the implementation of each function, along with its support of ProvenCore for security services.

Minimal Trusted Computing Base:
ProvenVisor maintains a minimal Trusted Computing Base (TCB), reducing the attack surface and enhancing the overall security posture of your embedded device.

Secure Inter-Guest Communications (IGC):
Inter-Guest Communications are performed only after explicit authorization, preventing unauthorized access between VMs and further enhancing security.

Strong Isolation Security Policy:
The hypervisor enforces a strict isolation security policy between all Virtual Machines (VMs), ensuring that each VM operates independently and securely.

Amenable to High-Level Security Certification:
ProvenVisor is designed with high-level security certification in mind, making it an ideal choice for applications requiring rigorous security assurances, such as Common Criteria EAL5 certification.
ProvenVisor and ProvenCore | The Perfect Duo for Enhanced Security
One of the key aspects of achieving robust security lies in eliminating exploitable vulnerabilities from the Trusted Computing Base (TCB). The TCB includes the security functions and the underlying operating system (OS) that these functions rely on. Therefore, the correctness and effectiveness ofs ecurity functions are intricately tied to the OS implementation, even when hypervisors are used.
ProvenCore, ProvenRun’s secure OS, can be used in combination to ProvenVisor to:

Enforce Sophisticated Security Policies:
ProvenCore works seamlessly with ProvenVisor to enforce advanced security policies. It provides precise control and filtering of communication between each guest OS and the outside world, bolstering the overall security posture.

Security-Sensitive Services
ProvenCore enables you to deploy security-sensitive applications by giving you access to a catalogue of trusted, ready-to-use applications (link to ProvenApps). This enables you to deliver critical security functions with the utmost reliability.

Holistic Device Protection:
Protect the security of the whole device (Secure Boot, Secure Firmware Update, etc.).
Hypervisors & | Security.
When multiple guest OSs are present, ProvenVisor can identify which guest OS issued a particular command, allowing ProvenCore to decide whether to allow or deny each command according to the identity of the guest OS. This configuration can be as fine-grained as allowing some services to be only accessible from a given subset of guests. For example, access to the Secure Storage can be limited to specific guests. More detail about ProvenCore here: ProvenCore
Hardware Requirements:
- ARM Architecture: Requires ARMv8-A architecture.
- IRQs: Requires a GICv2 or GICv3 (ARM’s generic interrupt controller) with virtualization extension.
- Power Control: Implements PSCI (ARM’s Power state Coordination interface) version 1.
- System MMU: Supports ARM’s System MMU.
- Flash and RAM Size: Requires less than 1MB for a simple configuration.
Discover | Security.
Discover how ProvenVisor can elevate the security of your embedded devices and provide the trust your applications need. Contact us at contact@provenrun.com to explore the power of ProvenVisor and secure your future projects.